Dark web links act as a directory for finding active search engines, dark web markets, and other weird onion services that we can find online.
The term dark web comes up many new stories and articles discussing ransomware and other cyberattacks, often alongside the deep web.
These terms are used interchangeably as synonyms which is is a mistake. The web can be grouped into three main sections.
Surface Web
The clear or surface web is the part that is open to indexing for search engines such as Google. The surface web is the web that most people know and use.
Estimates put this section at about six to ten percent of the deep web complete web infrastructure in use.
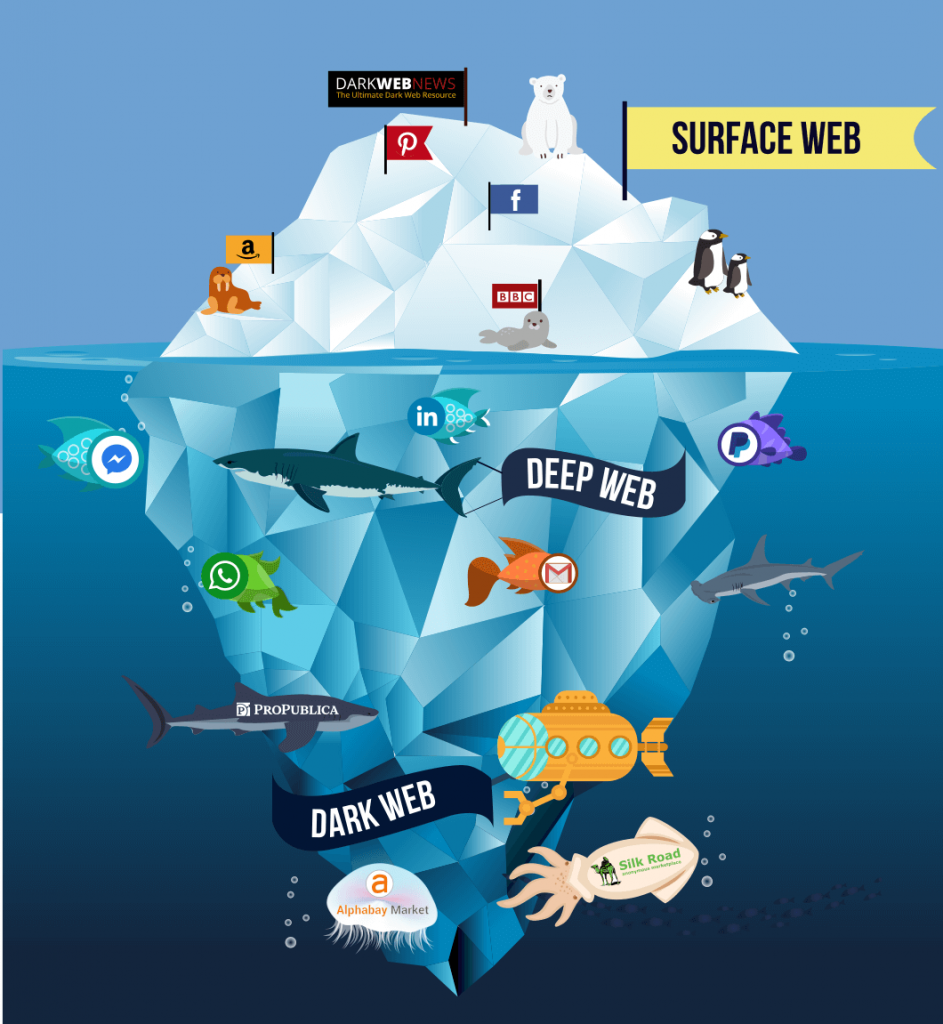
Deep Web
The media usually describes the Deep Web as a vast hidden area five thousand times larger than the surface web and loaded with criminals, but that is false. The Deep Web is not a place that is not hidden and consists of zero criminal activity. It simply accounts for the vast unindexed content online, raw data that Google doesn’t know about and doesn’t care about.
The deep web comprises all of the websites and applications that are not open to search engines for general indexing and discovery.
It includes private corporate sites, paywalled sites, health providers, and lots more. When you log into your online bank, you are using a deep website. The deep web makes up 80 to 90 percent of the whole worldwide web.
If you know about a site and have a login, you can browse the deep web via standard web browsers.
Dark Web
This dark web makes up approximately five percent of the web. Like the deep web, it is hidden from search engines. The small corner of the Internet comprises confidential information that the public cannot access.
Will you find crime? Yes, but not to the degree that media has claimed, and crime is neither the primary use of the darknet. The Department of Defense initially funded the Internet. As it became publicly facing the world wide web, new technologies on the Internet were created to ensure its use for defense.
So really, the dark web is just another tool, and government agencies use it all over the world along with journalists, dissidents, whistleblowers, and countries with hostile governments, and just regular folks who want to create and use anonymous online communities.
However, the dark web is also opaque to standard web browsers. To access dark websites requires specialized software such as the TOR browser or another darknet enabling tool.
There are some legitimate applications for the dark web, for example, by people living under authoritarian governments.
Like any place where human beings gather, there is an illegal activity. There are underground markets selling drugs, and many of these, like the Silk Road, essentially sell marijuana altogether. They serve a small fraction of the physical drug trade.
But for cybersecurity researchers, the dark web is the source of much planning and activity that leads to cyber attacks. Cybercriminals use dark markets to trade stolen information that can be used for further cyber-attacks.
It is also the place where stolen credit card details are bought and sold. Trade-in illicit electronic goods and illegal physical products also occur on the dark web markets. It’s a realm of the web that security researchers need to monitor. Using insights external threat protection tools, our industry-leading cybersecurity professionals monitor the whole web for risks and threats.
Tor Browser
In the TOR browser, URLs are a string of meaningless numbers and letters that end in .onion. Now, the Tor browser has initially been a U.S. Naval intelligence project. Then it became open source, and it allows anybody to browse the net without exposing their location.
The key to learning how Tor can be beneficial to you is understanding exactly how it functions.
There are many ways the Internet can recognize you, but the simplest and most basic method is via your IP address. By securing your IP address untraceable, Tor cloaks this identifying data of your online activity.
But how?
Well, in any regular online activity, you’re forming a direct connection connecting your computer and the site you’re accessing.
This digital line of communication is evident to online trackers and left broad public for anyone to see.
Tor, on the other hand, passes forward your data using layers of encryption. It does this by encrypting your IP address and routing it through several other worldwide computers that use the same TOR software.
Tor encrypts the application layer of your activity and redirects your transactions through a global network built up of thousands of relays or nodes. As your information moves from node to node, each decrypts the layer that exposes the next node the data has to pass through—all without revealing the locations of its last relay.
Download TOR Browser
You can download the Tor browser from the official Tor mirror – https://www.torproject.org/download/
Once installing the Tor Browser, the next is knowing the onion links to access the websites.
As we mentioned earlier, conventional search engines like Google cannot crawl tor websites. There are specific search engines designed only for onion searches.
Hidden WiKi Onion Link: http://wiki47qqn6tey4id7xeqb6l7uj6jueacxlqtk3adshox3zdohvo35vad.onion
Tor Search Engines
- OnionIndex Search Engine – OnionIndex Search Engine
- DuckDuckGo – DuckDuckGo Search Engine
- OnionLand – OnionLand Search
- tordex – tordex
- Torch – Torch
- Ahmia – Ahmia
- MetaGer – MetaGer – German Search
- haystak – haystak
Stores
- BlackMart – BlackMart
- Caribbean Cards – Caribbean Cards
- Psy Shop – Psy Shop – Drugs Market
- Cardzilla – Cardzilla
- 21 Million Club – 21 Million Club
- Bidencash – Bidencash
- Horizon Store – Horizon Store
- The Escrow – The Escrow
Email Providers
- ProtonMail – ProtonMail
- Alt Address – Alt Address
- secMail – secMail
- TorBox – TorBox
- Elude.in – Elude.in
- adunanza OnionMail Server – adunanza OnionMail Server
- tempmail + – tempmail +
- Onion Mail – Onion Mail
- DNMX – DNMX
- Mail2Tor – Mail2Tor
- Cockmail – Cockmail
- Confidant Mail – Confidant Mail
- Underwood’s Mail – Underwood’s Mail
Forums / Social / Chat
- dread – dread
- Deutschland im Deep Web Forum – Deutschland im Deep Web Forum
- Hidden Answers – Hidden Answers
- SuprBay – SuprBay: The PirateBay Forum
- Rutor – Rutor
- Lolita City – Lolita City
- Endchan – Endchan
- Raddle – Raddle
- MadIRC – MadIRC
- The Stock Insiders – The Stock Insiders
- Facebook – Facebook
- Ableonion – Ableonion
- Adamant – Adamant Decentralized messenger
- ~/XSS.is – XSS.is – Russian Hacking Forum
- HackTown – HackTown
- NZ Darknet Forum – NZ Darknet Market Forums
- The Calyx Institute (Jabber) – The Calyx Institute (Jabber)
- AN0NYM0US’z F0RUM – AN0NYM0US’z F0RUM
Onion Hosting / Domain Services / File Sharing
- Freedom Hosting Reloaded – Freedom Hosting Reloaded
- SporeStack – SporeStack
- Ablative Hosting – Ablative Hosting
- BlackCloud – BlackCloud
- ZeroBin – ZeroBin
- Keybase – Keybase
- SecureDrop – SecureDrop
- OnionShare – OnionShare
- NJALLA – OnionShare
- Ablative.Hosting – Ablative.Hosting
- OnionLand Hosting – OnionLand Hosting
- PRIVEX – PRIVEX Hosting
- Kowloon Hosting – Kowloon Hosting
- TorPress – TorPress, Free wordpress hosting
- Kaizushi – Kaizushi PHP, Django and Rails hosting and VPS
- OnionName – OnionName
- Garlic – Onion Generator – Garlic – Onion Generator
- TorShops – TorShops
VPN
- Mullvad VPN – Mullvad VPN
- cryptostorm – cryptostorm
- AirVPN – AirVPN
Whistleblowing / News
- ProPublica – ProPublica
- The Guardian – The Guardian | SecureDrop
- AfriLEAKS – AfriLEAKS
- The Intercept – The Intercept
- The CIA – CIA
- FLASHLIGHT – FLASHLIGHT
- VOA – VOA
- New York Times – The New York Times
- BBC – BBC
- bellingcat – bellingcat
- The Tor Times – The Tor Times
- RadioFreeEurope RadioLiberty – RadioFreeEurope RadioLiberty
- Organized Crime and Corruption Reporting Project – Organized Crime and Corruption Reporting Project
- Joker.buzz – Joker.buzz
- Privacy International – Privacy International
- DW News – DW News
- BalkanLeaks – BalkanLeaks
- BuzzFeed News – BuzzFeed News
Non English Websites
- Cebulka – Cebulka – Polish Onion Forum
- DimensionX – DimensionX – Another Polish Forum
- XMundo – XMundo – Turkish Dark Web Forum
- Germania – Germania – German Dark Web Forum
- Bibliothèque – Bibliothèque – French Darknet book library
Others
- RelateList – RelateList
- Hacker Game – Hacker Game
- Tech Learning Collective – Tech Learning Collective
- cryptostorm – cryptostorm
- PsychonauticsWIKI – PsychonauticsWIKI
- AgoraDesk – AgoraDesk
- Njalla – Njalla
- LocalMonero – LocalMonero
- The CIA – The CIA
- NCIDE Task Force – NCIDE Task Force
- National Police of the Netherlands – National Police of the Netherlands
- Fake ID Generator – Fake ID Generator
- Check your anonymity online – Check your anonymity online
- Beneath VT – Beneath VT
- Go Beyond – Go Beyond
- Deep Web Radio – Deep Web Radio
- DNM Bible – DNM Bible
- xmrguide – xmrguide
- JUST ANOTHER LIBRARY – JUST ANOTHER LIBRARY
- Bible4u – Go Beyond
- Zlibrary – Zlibrary
- Comic Book Library – Comic Book Library
- The Secret Story Archive – The Secret Story Archive
- Tor Project – Tor Project
- riseup – riseup
- Debain OS – Debain OS
- Russian Books – Russian Books
- Russian Torrent / Forum – Russian Torrent / Forum
- Sonic & Tails – Sonic & Tails
- phdcasino – phdcasino
- Webpage archive – Webpage archive
- OpenPGP Keyserver – OpenPGP Keyserver
- coinpayments – coinpayments
- Tor Metrics – Tor Metrics
- DEEPDOTWEB – DEEPDOTWEB
- superkuh – superkuh
- Connect – Connect
- We Fight Censorship – We Fight Censorship
- IIT Underground – IIT Underground
- Clockwise Library – Clockwise Library
Disclaimer
Any of the links listed above are not recommended, promoted, or affiliated with us. The links above are provided solely for educational reasons. Any losses and activities on the dark web are exclusively the responsibility of the user.
Safeguard yourself on TOR
It’s easy to browse dark websites and hidden wikis, but be aware that if you plan to do anything more than this, then there are some things you will need to take into account. If, for example, your mother requires drugs that cannot be legally obtained in your country so she can survive her illness – you’ll need to find a way of getting them illegally.
This means setting up encrypted email with a new email address, encrypting messages with PGP, using a pseudonym (so nobody knows who you are), setting up an anonymous bitcoin wallet (you can’t use the same one as your everyday bank account otherwise, it would leave evidence on banks’ servers), other safety precautions like disabling javascript in Tor Browser.
It is essential to be aware of the limitations of using Tor Browser. Your ISP and government know that you are browsing anonymously on Tor, and this alone may be enough for them to take notice. Recently, a court decision in the USA declared that simply logging on through Tor Browser constitutes sufficient probable cause for law enforcement officials to search any computer anywhere in the world.
Another vital precaution is to ensure that your .onion URLs are correct. Onion URLs generally contain a string of seemingly random letters and numbers. Once you are confident that you have the valid URL, save it in an encrypted note—the Tor browser will not cache it later.
It’s crucial to employ a second level of security (a paid VPN) before you use the Tor browser.
When you’re browsing the dark web, it is essential to keep security on your mind. Although hackers will always look for ways to hack unprotected computers and devices, they do not know who you are or where you live. Hackers may steal a personal document that has information about your life if given a chance.
As we already mentioned that you use a powerful VPN so nobody can hack you that easily, and suggest you browse the dark web with a device with no crucial file.
By that, hackers will target the computer or laptop of a person by searching for anyone holding sensitive information through these sorts of dark websites, and if they get hold of data about you, they can use it to blackmail you. If something has gone wrong or someone’s hurt using your data, any claim would be directed at you because you’re the owner of everything. You could get in a very big trouble by doing this.
As I already said in this article, illegal activities happen on the dark web, and some of the most significant crimes ever happen there. The FBI always tries to track people using it, but savvy users know how to protect themselves so that new users can be easy targets. To visit the dark web, make sure you maintain your security and access the Tor browser.
Understanding the Dark Web
In many ways, the dark web is no different from when it was first created during the late 20th century. There are many guides and how-to’s for getting started, but not much to do once things get underway. Much of its content is amateurish.
However, it’s much easier for individuals to create sites and draw attention. Tech giants, prominent media outlets, and governments have very little influence on the dark web as of 2021.
Like the Internet before it, the dark web has also gained a reputation as an illicit place. The dark web is insinuated in crimes, such as abuse and murder for hire through violence. Although the dark web helped campaigners who may otherwise be persecuted for their identities or political beliefs, those with both malicious intent & good intentions have used this new frontier to perpetrate acts of violence against others and themselves. In turn, authorities are using experiences from the unseen web to catch perpetrators of unethical activities.
It is crucial not to confuse the dark web with cryptocurrencies. While this online territory offers anonymity for its users, the websites there often only offer information and don’t allow commerce of any kind. However, it is possible to use cryptocurrencies without visiting the dark web by going through a cryptocurrency exchange or broker such as Coinbase.
The dark web and the deep web are often wrongly used interchangeably. The deep web includes all the pages that don’t pop up when running a search engine, such as private research databases. The darknet is just one part of the deep Internet that contains everything requiring a login, such as online banking, paysites, or file hosting services.
Dark Web Sites
Dark web sites do not use the .com or .co domain suffix. Instead, it uses a special-use top-level domain suffix known as .onion. This can enable browsing through browsers with Tor enabled, but other browsers won’t scan them.
The dark web is a dark and unknown place. There are, unfortunately, plenty of scammers who take advantage of people looking for dark websites. Even commerce sites that may have been around for years sometimes disappear because the owners decide to cash in on their scheme and flee once they collect enough funds from their victims.
Dark Web Trade
Sites on the dark web have become popular thanks to bitcoin, the cryptocurrency fueling two parties in a transaction without revealing any identities. “Bitcoin has been a major factor in the majority of the dark web, and the dark web has been a big part in the growth of bitcoin,” says Tiquet.
The dark web is fraught with danger for anyone, including those who want to buy things. It has a sense of anonymity that lures in scammers and thieves.
Though dark web commerce sites have the same features as any e-retail site, there are some critical differences. One of these is a quality check. When both buyers and sellers are anonymous, the trustworthiness of any rating method can be in question.
Even with a long track record, it’s possible for sellers to suddenly disappear with their customers’ cryptocurrencies only to show up again under a different alias later on.
Is the dark web illegal?
We don’t want to devise you with the idea that everything on the dark web is illegal or nefarious. Tor began as an anonymous communication network, and it now still serves a valuable purpose for helping people communicate in environments where free speech is suppressed. “A lot of people use it in nations where there’s eavesdropping or where internet access is criminalized,” Tiquet said.
If you’re looking for private information, the dark web provides plenty. There are encrypted email services, instructions on installing an anonymous operating system, and many tips if internet privacy is a concern.
Intel Exchange is a social media site where you can join conversations anonymously, participate in discussions about current events, and keep yourself up-to-date with the latest news. There have been several whistleblower sites that governments have shut down that now reside on the dark web, including an anonymous version of Wikileaks.
You can even find Facebook there, although it may not be quite what you’re expecting.


